Getting Started with WordPress Hosting
Featured
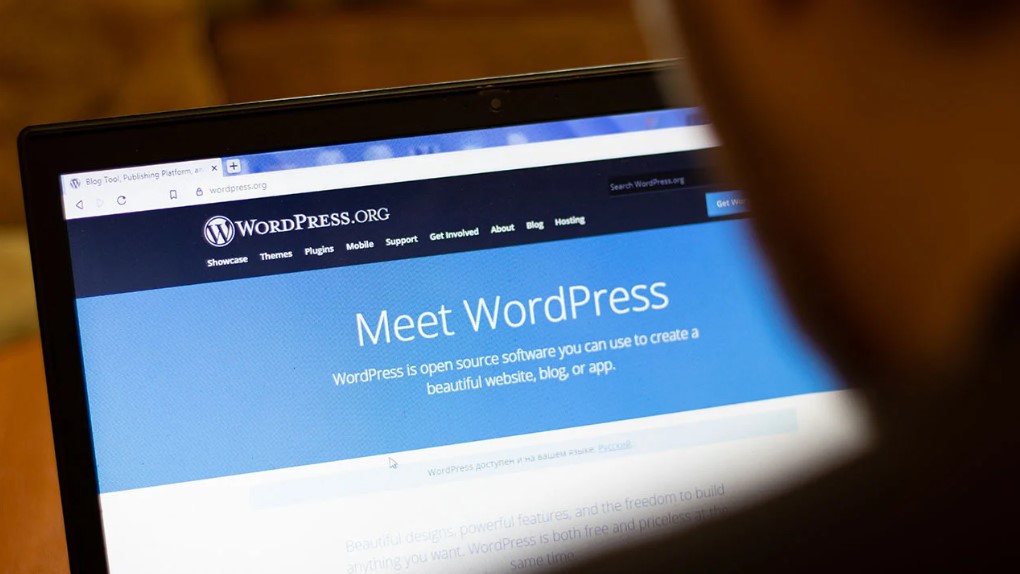
The process of Web Domain and Hosting is an umbrella term that deals with all types of hosting services. This includes shared hosting, VPS hosting, and others. WordPress hosting is a sub-category of web hosting that is specifically optimized for WordPress websites.
Many people who wish to build a website … Read the rest









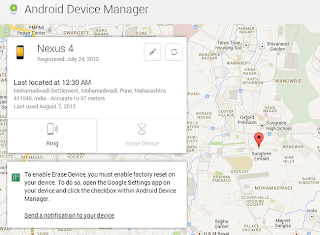 Unlocking, discovering or erasing a locked, misplaced or …
Unlocking, discovering or erasing a locked, misplaced or …  In case you are doing a enterprise associated to the computer repairs or the restore of mobile phones and tablets or any sort …
In case you are doing a enterprise associated to the computer repairs or the restore of mobile phones and tablets or any sort …  GDevelop is an open-supply, cross-platform recreation engine designed for everybody – it’s extensible, quick and simple to learn. It allows …
GDevelop is an open-supply, cross-platform recreation engine designed for everybody – it’s extensible, quick and simple to learn. It allows … .jpg) First on the list is Ars Technica, simply due to the date of inception. It’s not …
First on the list is Ars Technica, simply due to the date of inception. It’s not …